Table of Contents
BackBox Linux is a specialized Linux distribution based on Ubuntu, focused primarily on security and penetration testing. It's widely recognized in the cybersecurity community for its robust set of tools and efficient performance. As it is built on top of Ubuntu, it inherits Ubuntu's ease of use and reliability. This base ensures a stable and user-friendly experience, making it accessible even for those relatively new to Linux. Being open source, it also allows users to customize and improve the software. Similar to many Linux distributions, BackBox can be run in a live mode, meaning it can be booted from a DVD or USB drive without needing installation on the hard drive. This is particularly useful for forensic analysis.

BackBox - A Special Linux distribution for Security and Penetration Testers
Also Read: Elementary OS - Perfect Linux distribution to replace Windows and macOS
BackBox is designed to be lightweight, meaning it can run effectively on older hardware as well as modern systems, making it accessible for a wide range of users. It is designed for security analysis and penetration testing. It's a tool for ethical hackers, cybersecurity analysts, and IT professionals involved in the field of information security.
Key Features
- Security Tools: BackBox includes a comprehensive range of security and network analysis tools for penetration testing, vulnerability assessment, and cybersecurity. These tools are regularly updated.
- User Interface: BackBox typically uses the XFCE desktop environment, known for being lightweight and efficient, which makes it suitable for use on older hardware and in environments where performance is critical.
- Custom Kernel: Often, BackBox comes with a custom Linux kernel that is optimized for performance, particularly in network operations and security tasks.
- Repository Management: BackBox provides a well-organized and regularly updated software repository. The repositories are designed to be easy to use and include the latest stable versions of the most widely used hacking tools.
- Privacy Emphasis: Privacy tools and configurations are typically a part of the BackBox setup, allowing users to operate with an enhanced level of anonymity and privacy during penetration testing.
- Network Services Analysis: It includes tools for network services scanning and analysis, which are crucial in identifying vulnerabilities and security gaps in network infrastructures.
- Digital Forensics: It provides tools for digital forensics analysis, which are essential for investigating cybersecurity incidents and understanding complex threats.
- Customizable and Extensible: Users can customize their BackBox environment and extend its capabilities by adding additional tools and applications as needed.
- Community Support: BackBox has an active community, providing support and guidance, which is a great resource for beginners and experienced users alike.
- Educational Resource: The distribution can be used as an educational tool for those learning about information security and penetration testing.
Minimum Hardware Requirements
- Processor: A 32-bit or 64-bit processor.
- RAM: At least 1GB of RAM, although 2GB or more is recommended for better performance.
- Disk Space: Around 10GB of disk space. This provides enough space for the operating system and a basic set of tools.
- Graphics Card: Any basic graphics card that can support the display resolution you intend to use.
- Network Card: Compatible with Linux, as networking is a key aspect of penetration testing.
Installation Steps
To install Backbox linux, you have to first download it from official website. To download you can either do it through torrent file or you can directly download ISO image. You can also either pay for the image or you can download it for free by changing the value to 0 as you can see below. Once done, click on Download to start downloading the software.
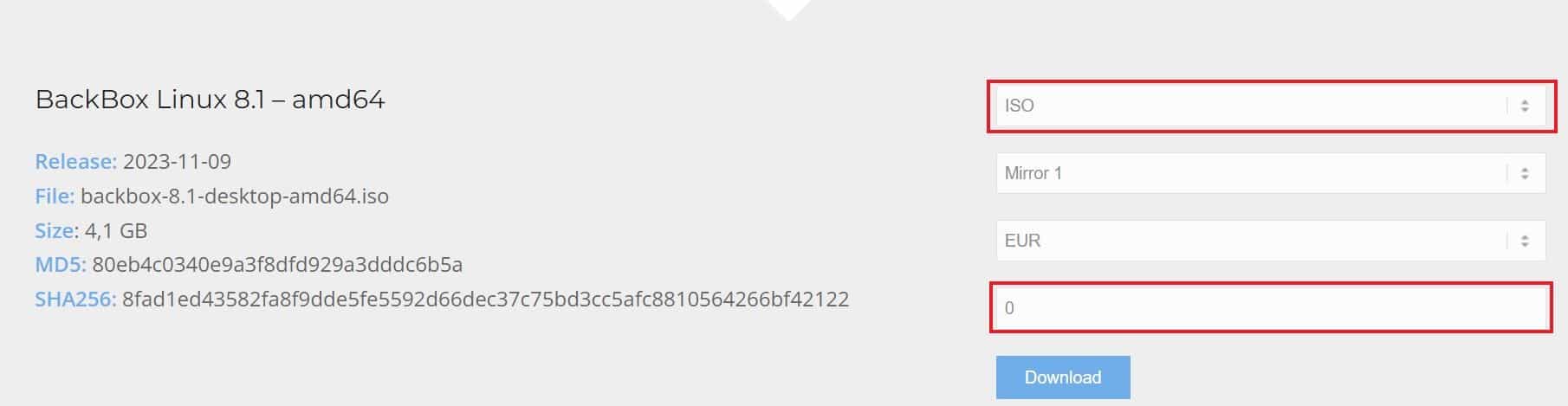
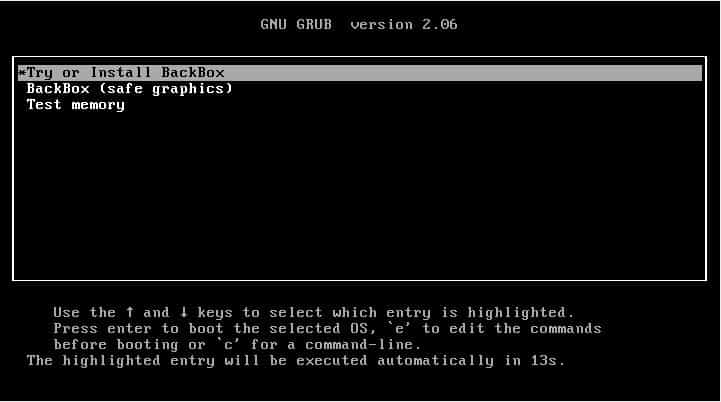
Once you have the ISO image downloaded, you can take it and make a bootable USB device to install the linux distribution on your system. If you are going to install on a virtual machine then you can do it directly from the ISO Image. For example, in our case, we are installing the distribution on VirtualBox by creating a virtual machine. Once the VM starts, it should load the boot loader as shown below. To proceed with installation, select Try or Install BackBox.
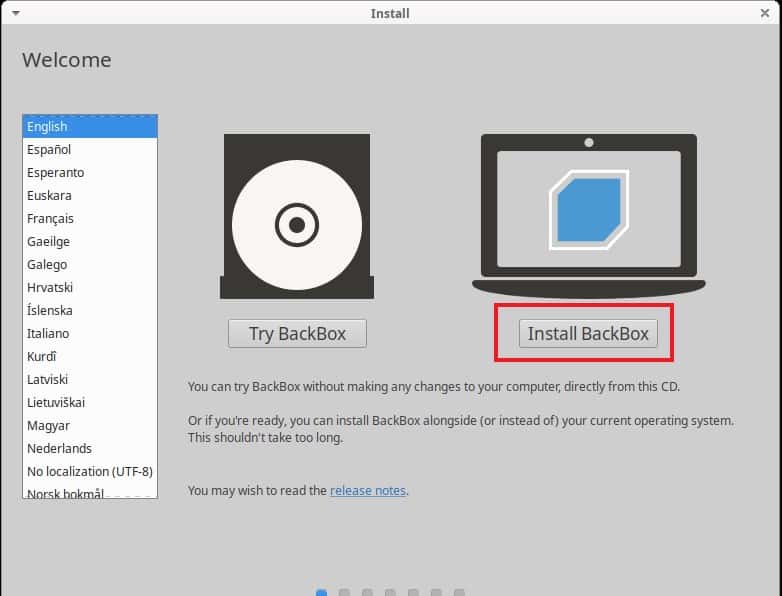
It will take you to the Install screen where you have select your language and click on Install BackBox as shown below.
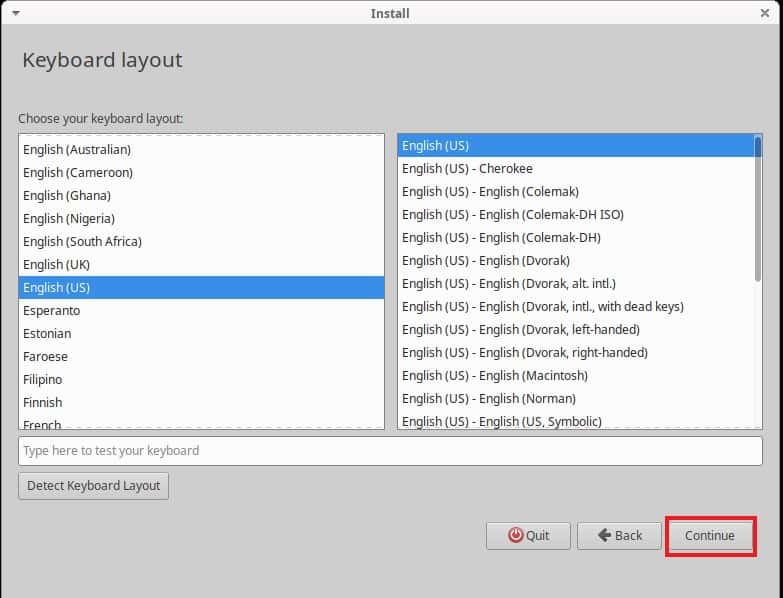
Then you have to select the Keyboard layout and click on Continue.
You will then be asked to select the apps that you would like to start with. You can either perform Normal installation which will install all the available packages or you can choose the Minimal installation which will install only basic packages and web browsers. You can also choose other available options such as Download updates while installing BackBox and Install third-party software for graphics and Wi-fi hardware and additional media formats. We are choosing Normal Installation with updates to download during installation as you can see below. You can choose the option which suits you the best and then click on Continue.
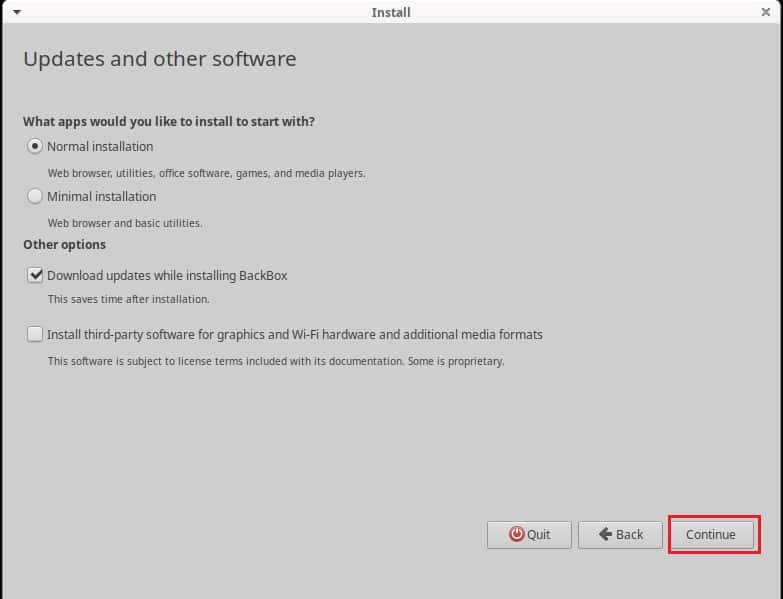
In the installation type, you can either choose to erase disk and install BackBox or you can create or resize partitions by yourself on the disk. We are going with the default selection i.e Erase disk and install BackBox to continue installing operating system on the disk. You can also make the selection as per your needs and requirements. Then click on Install Now.
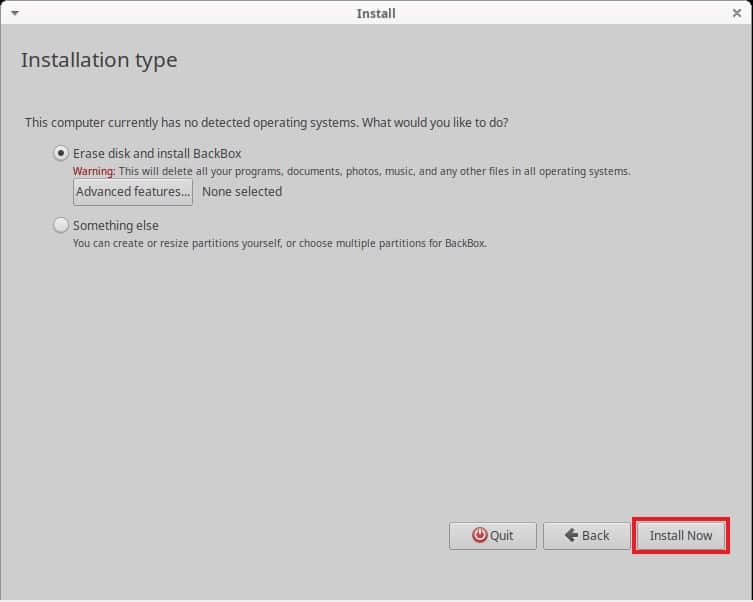
It will give you the notification to confirm your selection before making changes to disks. If you are sure then Click on Continue to confirm and proceed.
Next, you have to select the timezone you would like to use in your system. Then click on Continue to proceed.
Before starting the installation, you have to create an user account where you have specify the username, computer name and provide a strong password for authentication. Then click on Continue to finally start the installation.
You will see that the installation is started and progressing like below. Now you have to patiently wait for it to finish.
Once the installation is finished, it should show you below installation completion pop window. You can click on Restart Now to restart your machine.
You will then be asked to removed the installation medium and press Enter to continue. In a moment, you will see login screen where you have to provide the password to authenticate which you had given earlier during user account setup. Once given, click on Log In.
You will be logged in successfully and the desktop screen should look like below. This confirms successful installation on BackBox on your system.

Advantages
- Comprehensive Security Toolkit: BackBox provides a wide array of security and network analysis tools. This extensive toolkit is beneficial for penetration testing, vulnerability assessment, network analysis, and forensic analysis.
- Regular Updates and Maintenance: The tools and system are regularly updated. This ensures that you have the latest versions of security tools with the most recent patches and features.
- Lightweight and Efficient: Thanks to its use of the XFCE desktop environment, BackBox is lightweight and can run efficiently on older hardware as well as on modern systems. This makes it accessible for users with limited resources.
- User-Friendly Interface: Despite being a distribution geared towards professional use, BackBox has a user-friendly interface, making it accessible even for those who are relatively new to Linux.
- Customization and Flexibility: Users can customize their environment to suit their needs. This includes adding or removing tools, tweaking system performance, or changing the user interface.
- Live System Option: BackBox can be used as a live system, booting from a USB or DVD without installation. This is particularly useful for forensic purposes as it doesn't leave a footprint on the host system.
- Community and Support: BackBox has a supportive community and offers documentation, which is beneficial for troubleshooting and learning.
- Privacy-Oriented: The distribution includes tools and features that help maintain privacy and anonymity, which is crucial for security professionals.
- Educational Value: For students and individuals looking to learn about cybersecurity, BackBox can serve as an excellent educational tool. It provides practical experience with the tools and techniques used in the field.
- Professional Applications: For cybersecurity professionals, BackBox offers a reliable and stable platform for conducting security assessments and penetration tests in a professional setting.
- Cost-Effective: As an open-source platform, BackBox is free to use, making it a cost-effective solution for security testing.
- Forensic Capabilities: The distribution includes tools specifically for digital forensics, aiding in investigations and the analysis of digital evidence.
Drawbacks
While BackBox Linux is a powerful tool for cybersecurity professionals and enthusiasts, there are certain drawbacks and limitations to consider:-
- Learning Curve: For those new to Linux or penetration testing, BackBox can have a steep learning curve. Understanding how to effectively use the range of tools available requires time and effort.
- Specialized Focus: Being a distribution focused on security and penetration testing, it may not be as well-suited for general-purpose use as other Linux distributions. This specialization might limit its utility for users looking for a more versatile operating system.
- Resource Intensive: Although BackBox is designed to be lightweight, some of the more advanced tools and features can be resource-intensive. This might impact performance, particularly on older or less powerful hardware.
- Ethical and Legal Considerations: The tools included in BackBox are powerful and, if used improperly, can lead to ethical and legal issues. Users must have a clear understanding of the laws and regulations governing cybersecurity practices in their respective regions.
- Security Risks: Using a system loaded with penetration testing tools can sometimes pose a security risk. If not properly secured, it can be vulnerable to attacks, especially if users are inexperienced with securing a Linux environment.
- Hardware Compatibility: Like many Linux distributions, there can be issues with hardware compatibility, especially with very new or very specialized hardware components.
- Software Updates and Support: While regular updates are a feature of BackBox, they can also be a drawback if not managed properly. Frequent updates might require users to regularly adapt or reconfigure their setup.
- Community Size: While there is a community around BackBox, it is smaller than those of more mainstream Linux distributions. This can sometimes mean less readily available help or fewer resources for troubleshooting.
- Not Always Suitable for Beginners: Due to its specialized nature, BackBox might not be the best choice for beginners who are just starting out with Linux or cybersecurity.
- Potential for Misuse: The tools provided in BackBox can be misused for unethical hacking. It is essential that users adhere to ethical standards and use the distribution for lawful purposes only.
- Dependency on Command Line: Many of the tools and tasks in BackBox require command-line proficiency, which might be a barrier for users more accustomed to graphical interfaces.
Who should use
BackBox Linux is best suited for specific groups of users who require its specialized tools and features for security, networking, and penetration testing. The ideal users of BackBox are:-
- Cybersecurity Professionals: Security analysts, network administrators, and other cybersecurity professionals use BackBox for vulnerability assessment, network analysis, and security hardening. It provides a comprehensive suite of tools for conducting thorough security audits.
- Ethical Hackers and Penetration Testers: Ethical hackers and penetration testers use BackBox for simulating cyberattacks to identify vulnerabilities in systems and networks. Its extensive range of penetration testing tools makes it ideal for this purpose.
- IT Students and Researchers: Students and researchers in fields related to cybersecurity, network administration, and IT can benefit from BackBox as an educational tool. It offers a hands-on experience with professional-level tools in a controlled environment.
- Forensic Investigators: Digital forensic analysts and investigators use BackBox for forensics and data recovery. The distribution includes tools specifically designed for digital forensic analysis and investigation.
- Security Enthusiasts: Individuals who have a keen interest in cybersecurity and ethical hacking, and who wish to explore this field further, can use BackBox as a learning platform.
- System Administrators: System administrators can use BackBox for network and system analysis, troubleshooting, and ensuring that their infrastructure is secure from potential threats.
- Technology Educators and Trainers: Educators and trainers in the field of IT and cybersecurity can use BackBox as a teaching tool, providing students with practical experience in a wide range of security-related tasks.
