Table of Contents
In this article, we will see how to install snort on Ubuntu 22.04. Snort is a free and open source powerful network intrusion detection and prevention system that tracks and analyzes network packets in real time. It uses a rule based language to detect the anomaly and malicious activity in the network traffic. Snort helps spot Denial of Service(DoS) attacks, Distributed DoS attacks, Common Gateway Interface(CGI) attacks, buffer overflows and stealth port scans. It plays a vital role in inspecting and uncovering the malicious activity which usually goes undetected. It is also easy to install and deploy on almost all the famous platforms. Here we will see the steps to install snort on Ubuntu 22.04 system.

How to Install Snort on Ubuntu 22.04
Also Read: How to Install LuaJIT library on Ubuntu/Debian Linux
Step 1: Prerequisites
a) You should have a running Ubuntu 22.04 Server.
b) You should have sudo or root access to run privileged commands.
c) You should have apt or apt-get utility available in your Server.
d) You should also have wget and tar utility installed in your system.
Step 2: Update Your Server
Before installing snort package, it is highly recommended to sync your system with the latest available updates by using sudo apt update && sudo apt upgrade command as shown below.
cyberithub@ubuntu:~$ sudo apt update && sudo apt upgrade
Get:1 https://brave-browser-apt-release.s3.brave.com stable InRelease [7,547 B]
Hit:2 https://artifacts.elastic.co/packages/8.x/apt stable InRelease
Hit:3 https://dl.google.com/linux/chrome/deb stable InRelease
Hit:4 http://security.ubuntu.com/ubuntu jammy-security InRelease
Hit:5 http://in.archive.ubuntu.com/ubuntu jammy InRelease
Hit:6 http://in.archive.ubuntu.com/ubuntu jammy-updates InRelease
Hit:7 http://in.archive.ubuntu.com/ubuntu jammy-backports InRelease
Hit:8 https://ngrok-agent.s3.amazonaws.com buster InRelease
Fetched 7,547 B in 2s (3,170 B/s)
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
2 packages can be upgraded. Run 'apt list --upgradable' to see them.
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
Calculating upgrade... Done
The following packages have been kept back:
gjs libgjs0g
0 upgraded, 0 newly installed, 0 to remove and 2 not upgraded.
Step 3: Install Snort
In the next step, you can install snort by choosing any of the below methods depending on your requirements and needs.
a) Using Apt
The most easiest way to install snort is from default Ubuntu repo by using sudo apt install snort command as shown below. This will download and install the package along with all its dependencies.
cyberithub@ubuntu:~$ sudo apt install snort Reading package lists... Done Building dependency tree... Done Reading state information... Done The following additional packages will be installed: libdaq2 libdumbnet1 libluajit-5.1-2 libluajit-5.1-common libnetfilter-queue1 oinkmaster snort-common snort-common-libraries snort-rules-default Suggested packages: snort-doc The following NEW packages will be installed: libdaq2 libdumbnet1 libluajit-5.1-2 libluajit-5.1-common libnetfilter-queue1 oinkmaster snort snort-common snort-common-libraries snort-rules-default 0 upgraded, 10 newly installed, 0 to remove and 2 not upgraded. Need to get 2,349 kB of archives. After this operation, 10.6 MB of additional disk space will be used. Do you want to continue? [Y/n] Y Get:1 http://in.archive.ubuntu.com/ubuntu jammy/universe amd64 libluajit-5.1-common all 2.1.0~beta3+dfsg-6 [44.3 kB] Get:2 http://in.archive.ubuntu.com/ubuntu jammy/universe amd64 libluajit-5.1-2 amd64 2.1.0~beta3+dfsg-6 [238 kB] Get:3 http://in.archive.ubuntu.com/ubuntu jammy/universe amd64 snort-common-libraries amd64 2.9.15.1-6build1 [882 kB] Get:4 http://in.archive.ubuntu.com/ubuntu jammy/universe amd64 snort-rules-default all 2.9.15.1-6build1 [146 kB] Get:5 http://in.archive.ubuntu.com/ubuntu jammy/universe amd64 snort-common all 2.9.15.1-6build1 [49.7 kB] Get:6 http://in.archive.ubuntu.com/ubuntu jammy/universe amd64 libdumbnet1 amd64 1.12-10 [27.8 kB] Get:7 http://in.archive.ubuntu.com/ubuntu jammy/universe amd64 libnetfilter-queue1 amd64 1.0.5-2 [14.4 kB] Get:8 http://in.archive.ubuntu.com/ubuntu jammy/universe amd64 libdaq2 amd64 2.0.7-5 [83.5 kB] Get:9 http://in.archive.ubuntu.com/ubuntu jammy/universe amd64 snort amd64 2.9.15.1-6build1 [792 kB] Get:10 http://in.archive.ubuntu.com/ubuntu jammy/universe amd64 oinkmaster all 2.0-4.1 [71.8 kB] .......................................................................
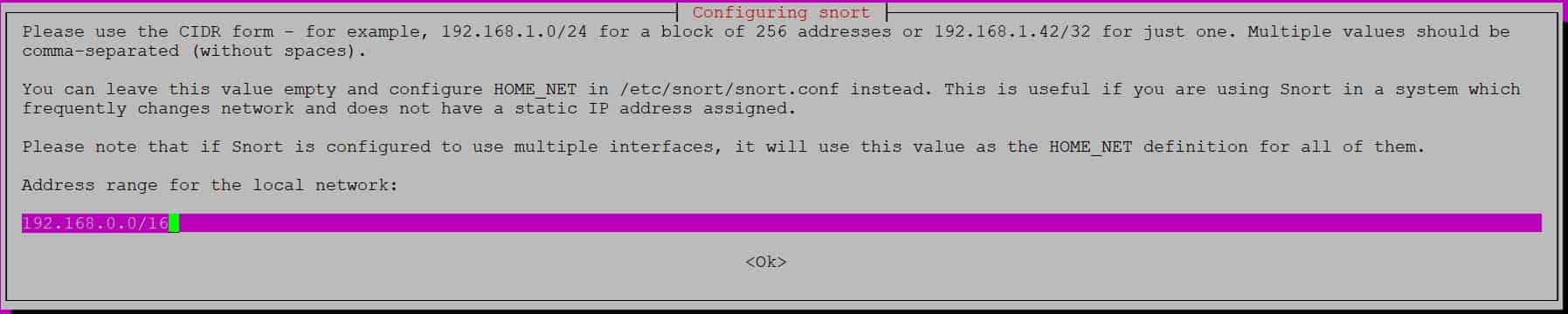
If you are installing snort for the very first time then you will be asked to configure snort by providing the local network address range as shown below. By default, it will take 192.168.0.0/16 address range. You can also leave this empty and instead configure HOME_NET in /etc/snort/snort.conf file. Then Press tab to click on Ok. In a while, you will see snort installation gets completed successfully.
b) Using Source Code
Another method that you can use to install snort is through the source code. But before that you have to first install LibDAQ data acquisition library as a prerequisites. For that, you have to visit snort official website and download the libdaq source code using below wget command.
cyberithub@ubuntu:~$ wget https://www.snort.org/downloads/snortplus/libdaq-3.0.12.tar.gz --2023-10-08 11:14:32-- https://www.snort.org/downloads/snortplus/libdaq-3.0.12.tar.gz Resolving www.snort.org (www.snort.org)... 104.18.138.9, 104.18.139.9, 2606:4700::6812:8b09, ... Connecting to www.snort.org (www.snort.org)|104.18.138.9|:443... connected. HTTP request sent, awaiting response... 302 Found Location: https://snort-org-site.s3.amazonaws.com/production/release_files/files/000/035/321/original/libdaq-3.0.12.tar.gz?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAU7AK5ITMJQBJPARJ%2F20231008%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20231008T054433Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Signature=1334362ba34ba12ac356e25870317b68ce2ba4d2dea4b33c8597f91a48811e2e [following] --2023-10-08 11:14:33-- https://snort-org-site.s3.amazonaws.com/production/release_files/files/000/035/321/original/libdaq-3.0.12.tar.gz?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAU7AK5ITMJQBJPARJ%2F20231008%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20231008T054433Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Signature=1334362ba34ba12ac356e25870317b68ce2ba4d2dea4b33c8597f91a48811e2e Resolving snort-org-site.s3.amazonaws.com (snort-org-site.s3.amazonaws.com)... 52.217.167.97, 3.5.9.205, 16.182.96.193, ... Connecting to snort-org-site.s3.amazonaws.com (snort-org-site.s3.amazonaws.com)|52.217.167.97|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 167878 (164K) [binary/octet-stream] Saving to: ‘libdaq-3.0.12.tar.gz’ libdaq-3.0.12.tar.gz 100%[============================================================================>] 163.94K 230KB/s in 0.7s 2023-10-08 11:14:35 (230 KB/s) - ‘libdaq-3.0.12.tar.gz’ saved [167878/167878]
Extract the file by using tar -xzvf libdaq-3.0.12.tar.gz command as shown below.
cyberithub@ubuntu:~$ tar -xzvf libdaq-3.0.12.tar.gz
libdaq-3.0.12/
libdaq-3.0.12/.gitignore
libdaq-3.0.12/COPYING
libdaq-3.0.12/ChangeLog-2.x
libdaq-3.0.12/LICENSE
libdaq-3.0.12/Makefile.am
libdaq-3.0.12/README.md
libdaq-3.0.12/api/
libdaq-3.0.12/api/Makefile.am
libdaq-3.0.12/api/daq.h
libdaq-3.0.12/api/daq_api_internal.h
libdaq-3.0.12/api/daq_base.c
libdaq-3.0.12/api/daq_base_api.c
libdaq-3.0.12/api/daq_common.h
libdaq-3.0.12/api/daq_config.c
....................................
Then switch to directory libdaq-3.0.12 by using cd libdaq-3.0.12 command.
cyberithub@ubuntu:~$ cd libdaq-3.0.12
To generate configure script, run ./bootstrap as shown below.
cyberithub@ubuntu:~/libdaq-3.0.12$ ./bootstrap
+ autoreconf -ivf --warnings=all
autoreconf: export WARNINGS=all
autoreconf: Entering directory '.'
autoreconf: configure.ac: not using Gettext
autoreconf: running: aclocal --force -I m4
autoreconf: configure.ac: tracing
autoreconf: running: libtoolize --copy --force
libtoolize: putting auxiliary files in '.'.
libtoolize: copying file './ltmain.sh'
libtoolize: putting macros in AC_CONFIG_MACRO_DIRS, 'm4'.
libtoolize: copying file 'm4/libtool.m4'
libtoolize: copying file 'm4/ltoptions.m4'
libtoolize: copying file 'm4/ltsugar.m4'
libtoolize: copying file 'm4/ltversion.m4'
libtoolize: copying file 'm4/lt~obsolete.m4'
autoreconf: configure.ac: not using Intltool
autoreconf: configure.ac: not using Gtkdoc
autoreconf: running: aclocal --force -I m4
autoreconf: running: /usr/bin/autoconf --force
configure.ac:27: warning: The macro `AC_PROG_CC_C99' is obsolete.
configure.ac:27: You should run autoupdate.
./lib/autoconf/c.m4:1659: AC_PROG_CC_C99 is expanded from...
configure.ac:27: the top level
autoreconf: running: /usr/bin/autoheader --force
autoreconf: running: automake --add-missing --copy --force-missing
configure.ac:26: installing './compile'
configure.ac:19: installing './missing'
api/Makefile.am: installing './depcomp'
autoreconf: Leaving directory '.'
You can see that configure script generated in current directory. Now run the ./configure script to check the availability of all the packages, libraries and other tools required for installation.
cyberithub@ubuntu:~/libdaq-3.0.12$ ./configure
checking for a BSD-compatible install... /usr/bin/install -c
checking whether build environment is sane... yes
checking for a race-free mkdir -p... /usr/bin/mkdir -p
checking for gawk... no
checking for mawk... mawk
checking whether make sets $(MAKE)... yes
checking whether make supports nested variables... yes
checking for gcc... gcc
checking whether the C compiler works... yes
checking for C compiler default output file name... a.out
checking for suffix of executables...
checking whether we are cross compiling... no
checking for suffix of object files... o
checking whether the compiler supports GNU C... yes
checking whether gcc accepts -g... yes
..............................................
Once the required configuration is checked, compile the source code to generate binaries by running make command as shown below.
cyberithub@ubuntu:~/libdaq-3.0.12$ make
make all-recursive
make[1]: Entering directory '/home/cyberithub/libdaq-3.0.12'
Making all in api
make[2]: Entering directory '/home/cyberithub/libdaq-3.0.12/api'
/bin/bash ../libtool --tag=CC --mode=compile gcc -DHAVE_CONFIG_H -I. -I.. -fvisibility=hidden -Wall -Wmissing-declarations -Wpointer-arith -Wcast-align -Wcast-qual -Wformat -Wformat-nonliteral -Wformat-security -Wundef -Wwrite-strings -Wextra -Wsign-compare -Wno-unused-parameter -fno-strict-aliasing -fdiagnostics-show-option -Wstrict-prototypes -Wmissing-prototypes -Wold-style-definition -Wnested-externs -g -O2 -MT libdaq_la-daq_base.lo -MD -MP -MF .deps/libdaq_la-daq_base.Tpo -c -o libdaq_la-daq_base.lo `test -f 'daq_base.c' || echo './'`daq_base.c
libtool: compile: gcc -DHAVE_CONFIG_H -I. -I.. -fvisibility=hidden -Wall -Wmissing-declarations -Wpointer-arith -Wcast-align -Wcast-qual -Wformat -Wformat-nonliteral -Wformat-security -Wundef -Wwrite-strings -Wextra -Wsign-compare -Wno-unused-parameter -fno-strict-aliasing -fdiagnostics-show-option -Wstrict-prototypes -Wmissing-prototypes -Wold-style-definition -Wnested-externs -g -O2 -MT libdaq_la-daq_base.lo -MD -MP -MF .deps/libdaq_la-daq_base.Tpo -c daq_base.c -fPIC -DPIC -o .libs/libdaq_la-daq_base.o
libtool: compile: gcc -DHAVE_CONFIG_H -I. -I.. -fvisibility=hidden -Wall -Wmissing-declarations -Wpointer-arith -Wcast-align -Wcast-qual -Wformat -Wformat-nonliteral -Wformat-security -Wundef -Wwrite-strings -Wextra -Wsign-compare -Wno-unused-parameter -fno-strict-aliasing -fdiagnostics-show-option -Wstrict-prototypes -Wmissing-prototypes -Wold-style-definition -Wnested-externs -g -O2 -MT libdaq_la-daq_base.lo -MD -MP -MF .deps/libdaq_la-daq_base.Tpo -c daq_base.c -o libdaq_la-daq_base.o >/dev/null 2>&1
...................................................
After successfully generating the binaries, you can install them using sudo make install command as shown below.
cyberithub@ubuntu:~/libdaq-3.0.12$ sudo make install
Making install in api
make[1]: Entering directory '/home/cyberithub/libdaq-3.0.12/api'
make[2]: Entering directory '/home/cyberithub/libdaq-3.0.12/api'
/usr/bin/mkdir -p '/usr/local/lib'
/bin/bash ../libtool --mode=install /usr/bin/install -c libdaq.la '/usr/local/lib'
libtool: install: /usr/bin/install -c .libs/libdaq.so.3.0.0 /usr/local/lib/libdaq.so.3.0.0
libtool: install: (cd /usr/local/lib && { ln -s -f libdaq.so.3.0.0 libdaq.so.3 || { rm -f libdaq.so.3 && ln -s libdaq.so.3.0.0 libdaq.so.3; }; })
libtool: install: (cd /usr/local/lib && { ln -s -f libdaq.so.3.0.0 libdaq.so || { rm -f libdaq.so && ln -s libdaq.so.3.0.0 libdaq.so; }; })
libtool: install: /usr/bin/install -c .libs/libdaq.lai /usr/local/lib/libdaq.la
libtool: install: /usr/bin/install -c .libs/libdaq.a /usr/local/lib/libdaq.a
libtool: install: chmod 644 /usr/local/lib/libdaq.a
libtool: install: ranlib /usr/local/lib/libdaq.a
libtool: finish: PATH="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin:/sbin" ldconfig -n /usr/local/lib
....................................................
Once LibDAQ is installed, you can now download the latest available snort 3 source code by using below wget command.
cyberithub@ubuntu:~$ wget https://www.snort.org/downloads/snortplus/snort3-3.1.71.0.tar.gz --2023-10-08 11:09:26-- https://www.snort.org/downloads/snortplus/snort3-3.1.71.0.tar.gz Resolving www.snort.org (www.snort.org)... 104.18.138.9, 104.18.139.9, 2606:4700::6812:8a09, ... Connecting to www.snort.org (www.snort.org)|104.18.138.9|:443... connected. HTTP request sent, awaiting response... 302 Found Location: https://snort-org-site.s3.amazonaws.com/production/release_files/files/000/035/322/original/snort3-3.1.71.0.tar.gz?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAU7AK5ITMJQBJPARJ%2F20231008%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20231008T053927Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Signature=133d4392d29d41efb41b6e715b0e6aa84a30cb9d210b22ea398730be5076cedd [following] --2023-10-08 11:09:27-- https://snort-org-site.s3.amazonaws.com/production/release_files/files/000/035/322/original/snort3-3.1.71.0.tar.gz?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAU7AK5ITMJQBJPARJ%2F20231008%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20231008T053927Z&X-Amz-Expires=3600&X-Amz-SignedHeaders=host&X-Amz-Signature=133d4392d29d41efb41b6e715b0e6aa84a30cb9d210b22ea398730be5076cedd Resolving snort-org-site.s3.amazonaws.com (snort-org-site.s3.amazonaws.com)... 52.217.40.108, 3.5.29.237, 52.217.201.225, ... Connecting to snort-org-site.s3.amazonaws.com (snort-org-site.s3.amazonaws.com)|52.217.40.108|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 3262948 (3.1M) [binary/octet-stream] Saving to: ‘snort3-3.1.71.0.tar.gz’ snort3-3.1.71.0.tar.gz 100%[============================================================================>] 3.11M 1.43MB/s in 2.2s 2023-10-08 11:09:30 (1.43 MB/s) - ‘snort3-3.1.71.0.tar.gz’ saved [3262948/3262948]
After downloading the file, you can extract it by using tar -xzvf snort3-3.1.71.0.tar.gz command as shown below. It will extract all the files under snort3-3.1.71.0 directory.
cyberithub@ubuntu:~$ tar -xzvf snort3-3.1.71.0.tar.gz
Switch to the directory using cd snort3-3.1.71.0 command.
cyberithub@ubuntu:~$ cd snort3-3.1.71.0
Then run ./configure_cmake.sh script to check the availability of all the libraries and packages required for installation.
cyberithub@ubuntu:~/snort3-3.1.71.0$ ./configure_cmake.sh
./configure_cmake.sh: 486: [: Illegal number:
Build Directory : build
Source Directory: /home/cyberithub/snort3-3.1.71.0
-- The CXX compiler identification is Clang 14.0.0
-- The C compiler identification is GNU 11.4.0
-- Detecting CXX compiler ABI info
-- Detecting CXX compiler ABI info - done
-- Check for working CXX compiler: /usr/bin/c++ - skipped
-- Detecting CXX compile features
-- Detecting CXX compile features - done
-- Detecting C compiler ABI info
-- Detecting C compiler ABI info - done
..............................................
-- Configuring done
-- Generating done
-- Build files have been written to: /home/cyberithub/snort3-3.1.71.0/build
After building all the files, switch to build directory using cd build command.
cyberithub@ubuntu:~/snort3-3.1.71.0$ cd build
Then run make command to compile all the target files based on Makefile rule.
cyberithub@ubuntu:~/snort3-3.1.71.0/build$ make
[ 0%] Building CXX object src/connectors/tcp_connector/CMakeFiles/tcp_connector.dir/tcp_connector.cc.o
[ 0%] Building CXX object src/connectors/tcp_connector/CMakeFiles/tcp_connector.dir/tcp_connector_module.cc.o
[ 0%] Built target tcp_connector
[ 0%] Building CXX object src/actions/CMakeFiles/ips_actions.dir/actions.cc.o
[ 0%] Building CXX object src/actions/CMakeFiles/ips_actions.dir/ips_actions.cc.o
[ 1%] Building CXX object src/actions/CMakeFiles/ips_actions.dir/act_alert.cc.o
[ 1%] Building CXX object src/actions/CMakeFiles/ips_actions.dir/act_block.cc.o
[ 1%] Building CXX object src/actions/CMakeFiles/ips_actions.dir/act_drop.cc.o
[ 1%] Building CXX object src/actions/CMakeFiles/ips_actions.dir/act_file_id.cc.o
[ 1%] Building CXX object src/actions/CMakeFiles/ips_actions.dir/act_log.cc.o
[ 1%] Building CXX object src/actions/CMakeFiles/ips_actions.dir/act_pass.cc.o
[ 1%] Building CXX object src/actions/CMakeFiles/ips_actions.dir/act_reject.cc.o
[ 1%] Building CXX object src/actions/CMakeFiles/ips_actions.dir/act_replace.cc.o
[ 1%] Building CXX object src/actions/CMakeFiles/ips_actions.dir/act_react.cc.o
[ 1%] Built target ips_actions
[ 2%] Building CXX object src/codecs/CMakeFiles/codecs.dir/codec_api.cc.o
[ 2%] Building CXX object src/codecs/CMakeFiles/codecs.dir/codec_module.cc.o
.................................................
[100%] Built target snort2lua
[100%] Building C object daqs/CMakeFiles/daq_file.dir/daq_file.c.o
[100%] Linking C shared module daq_file.so
[100%] Built target daq_file
[100%] Building C object daqs/CMakeFiles/daq_hext.dir/daq_hext.c.o
[100%] Linking C shared module daq_hext.so
[100%] Built target daq_hext
Finally run sudo make install command to install all the binaries.
cyberithub@ubuntu:~/snort3-3.1.71.0/build$ sudo make install
[sudo] password for cyberithub:
Consolidate compiler generated dependencies of target tcp_connector
[ 0%] Built target tcp_connector
Consolidate compiler generated dependencies of target ips_actions
[ 1%] Built target ips_actions
Consolidate compiler generated dependencies of target codecs
[ 2%] Built target codecs
Consolidate compiler generated dependencies of target root_codecs
[ 2%] Built target root_codecs
Consolidate compiler generated dependencies of target link_codecs
[ 3%] Built target link_codecs
Consolidate compiler generated dependencies of target ip_codecs
[ 5%] Built target ip_codecs
Consolidate compiler generated dependencies of target misc_codecs
[ 6%] Built target misc_codecs
Consolidate compiler generated dependencies of target control
[ 6%] Built target control
................................
-- Installing: /usr/local/snort/share/doc/snort/snort2lua.txt
-- Installing: /usr/local/snort/share/doc/snort/snort_upgrade.txt
-- Installing: /usr/local/snort/share/doc/snort/config_changes.txt
-- Installing: /usr/local/snort/share/doc/snort/snort_upgrade.text
-- Installing: /usr/local/snort/share/doc/snort/snort_devel.txt
-- Installing: /usr/local/snort/share/doc/snort/extending.txt
-- Installing: /usr/local/snort/share/doc/snort/style.txt
Since by default snort gets installed under /usr/local/snort location which might not be set under PATH environment variable so to make the snort binary path visible to the system, you have to set the path using below export command.
cyberithub@ubuntu:~/snort3-3.1.71.0/build$ export PATH=$PATH:/usr/local/snort/bin
To make above changes permanent, set the path in either ~/.profile or ~/.bashrc file. Then logout and login to the system to refresh the changes.
Step 4: Verify Installation
If you installed the package through apt package manager then you can check all the installed files path by using dpkg -L snort command as shown below.
cyberithub@ubuntu:~$ dpkg -L snort
/.
/etc
/etc/cron.daily
/etc/default
/etc/default/snort
/etc/init.d
/etc/init.d/snort
/etc/logrotate.d
/etc/logrotate.d/snort
/etc/ppp
/etc/ppp/ip-down.d
/etc/ppp/ip-down.d/snort
/etc/ppp/ip-up.d
/etc/ppp/ip-up.d/snort
/etc/snort
/usr
/usr/bin
/usr/bin/u2boat
/usr/bin/u2spewfoo
/usr/sbin
/usr/sbin/appid_detector_builder.sh
/usr/sbin/snort
......................................................
Step 5: Check Version
You can also check and verify the current installed version by using snort --version command as shown below.
cyberithub@ubuntu:~$ snort --version
''_ -*> Snort! <*-
o" )~ Version 2.9.15.1 GRE (Build 15125)
'''' By Martin Roesch & The Snort Team: http://www.snort.org/contact#team
Copyright (C) 2014-2019 Cisco and/or its affiliates. All rights reserved.
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using libpcap version 1.10.1 (with TPACKET_V3)
Using PCRE version: 8.39 2016-06-14
Using ZLIB version: 1.2.11
Step 6: Uninstall Snort
Once you are done using snort, you can choose to uninstall it from your system by using sudo apt remove snort command as shown below. If you are looking to remove all dependencies along with snort package then use --auto-remove option as well with below command.
cyberithub@ubuntu:~$ sudo apt remove snort [sudo] password for cyberithub: Reading package lists... Done Building dependency tree... Done Reading state information... Done The following packages were automatically installed and are no longer required: libdaq2 libdumbnet1 libluajit-5.1-2 libluajit-5.1-common libnetfilter-queue1 oinkmaster snort-common snort-common-libraries snort-rules-default Use 'sudo apt autoremove' to remove them. The following packages will be REMOVED: snort 0 upgraded, 0 newly installed, 1 to remove and 2 not upgraded. After this operation, 2,079 kB disk space will be freed. Do you want to continue? [Y/n] Y (Reading database ... 242523 files and directories currently installed.) Removing snort (2.9.15.1-6build1) ... * Stopping Network Intrusion Detection System snort [ OK ] Processing triggers for man-db (2.10.2-1) ...

